Table of Contents
What is klouddb_shield ?
Klouddb_Shield is an open source security tool that checks for CIS compliance( https://www.cisecurity.org/cis-benchmarks/) . Currently we check for 8 RDS controls , 32 controls(Postgres) , 46 MySQL controls – a total of 86 checks as of today and we plan to add more checks soon
How to run this tool on my server ?
You can directly download the package from releases section of repo https://github.com/klouddb/klouddbshield and install the package (for example – rpm for centos ; deb package for Ubuntu etc..). NOTE – You need to install this on a bastion host or ec2 machine which has access to your RDS instances
Once you install it , you need to configure your AWS cli before running the tool(access key , secret key , region etc..). Once AWS cli is configured you can execute command as shown below(NOTE – It only runs for one region at a time ). You need to select Option 3 for RDS
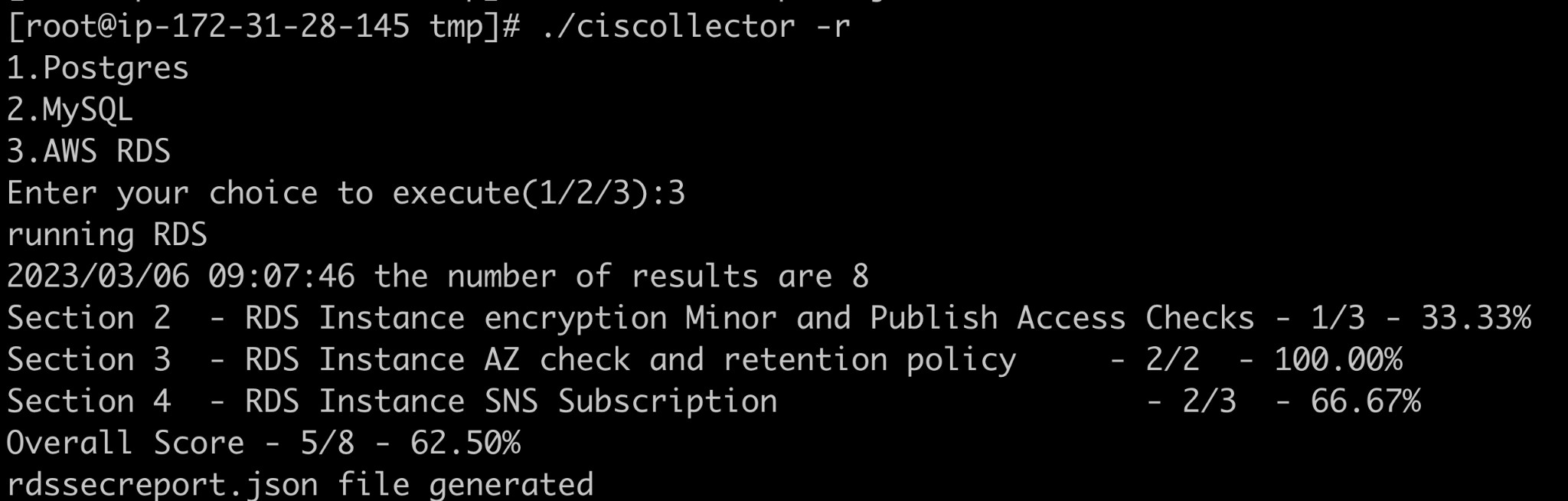
How to read the json output file generated ?
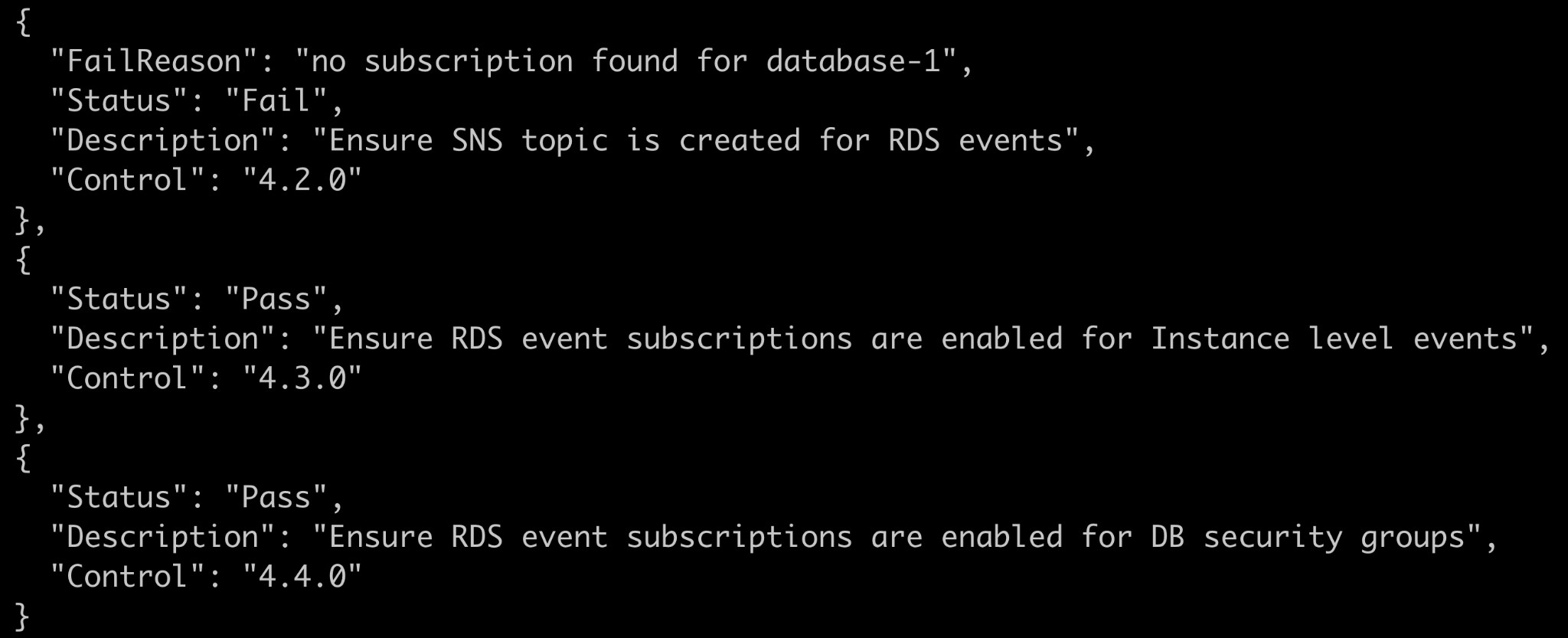
For each control you will get a PASS or FAIL as status . If it is FAIL you also can see the reason for failure . For example in below snapshot you can see that SNS topic control failed and the reason for failure is given
Ensure that encryption is enabled for RDS instances
Amazon RDS encrypted DB instances use the industry standard AES-256 encryption algorithm to encrypt your data on the server that hosts your Amazon RDS DB instances . Databases are likely to hold sensitive and critical data, it is highly recommended to implement encryption in order to protect your data from unauthorized access or disclosure
This check validates if all your RDS instances are encrypted or not . If you get a FAIL for this control it is a big red flag and it is highly recommended that you turn on encryption for your RDS instances
Ensure that auto minor version upgrade is enabled for RDS instances
Ensure that RDS database instances have the Auto Minor Version Upgrade flag enabled in order to automatically receive minor engine upgrades during the specified maintenance window. So, RDS instances can get the new features, bug fixes, and security patches for their database engines
You can also manually validate with a cli command like below
aws rds describe-db-instances –region –db-instance-identifier –query ‘DBInstances[*].AutoMinorVersionUpgrade’
Ensure that public address is not given to RDS instance
Ensure that no public-facing RDS database instances are provisioned in your AWS account and restrict unauthorized access in order to minimize security risks.
If any of your RDS instances are public facing , Kindly rectify this issue ASAP
Ensure that Multi-AZ enabled for high availability
Multi-AZ enables high availability – This check ensures that a failure of single instance will not impact your availability (Note – Multi-AZ may not be needed for test environments . It all depends on the criticality of app , business condition etc..)
You can also manually validate with a cli command like below
aws rds describe-db-instances –query “DBInstances[*].{MultiAZ:MultiAZ, DBInstanceIdentifier:DBInstanceIdentifier}”
Ensure Relational Database Service backup retention policy is set
It is better to have good backup retention policy set for your RDS instances – Having old backups will help you in recovering your data . This check ensures that your retention policy is set to a value equal or greater than 7 days
Ensure SNS topic is created for RDS events
For the RDS event subscriptions to be able to send out notifications, a SNS topic should be created. Amazon Simple Notification Service (Amazon SNS) is a web service that coordinates and manages the delivery or sending of messages to subscribing endpoints or clients.
This check ensures that you have sns topic and event subscriptions for your RDS instances
Ensure RDS event subscriptions are enabled for Instance level events
Below are some of the instance level events we check here – It is better to have event subscriptions for all of below
- ‘deletion’
- ‘failure’
- ‘failover’
- ‘low storage’
- ‘Maintenance’
- ‘notification’
Ensure RDS event subscriptions are enabled for DB security groups
This check ensures that event subscriptions are enabled for DB security groups. Security group controls the access to RDS instance and changing it should be notified
Future releases
We are planning to add more RDS checks in future releases
References
Control documentation reference used is given below
https://www.cisecurity.org/cis-benchmarks/
Summary
We released KloudDB Shield 1.2(first version that includes RDS checks) today . Please give it a try and pass your feedback . We spent ton of time to develop this tool and we plan to enhance this tool based on user feedback
Also check our performance articles –Pg_fincore and pg_buffercache to troubleshoot performance issues , Pgbouncer multiple instances(How we increased our TPS using multiple instances) , Postgres and temporary files , Pgpool and performance tuning, How we improved Lambda performance by 130x etc..
Looking for Postgres support ? Please reach us at support@klouddb.io
